With phishing attacks escalating globally, they’ve become one of the most sophisticated threats online. The FBI recently reported that Americans lost over $12.5 billion in phishing scams in 2023 alone. Although email phishing is the most common, there are now numerous methods attackers use to capture sensitive information. This article delves into various phishing attack types, explains their unique tactics, and provides guidance on safeguarding against each.
What is Phishing?

Image Credit: ShutterStock
Phishing refers to a range of tactics that cybercriminals use to trick individuals into disclosing personal, financial, or login information. Attackers often impersonate reputable organizations or known contacts, creating an appearance of legitimacy that can prompt users to take risky actions like clicking malicious links, downloading infected files, or giving out personal information.
The Rise of Phishing Attacks
The surge in online activity has intensified phishing schemes. Today’s phishing emails and texts look almost indistinguishable from legitimate messages, largely due to generative AI and other sophisticated tools. Unlike in the past, when phishing emails were poorly written and easier to spot, hackers now craft highly convincing messages that can fool even the most tech-savvy users.
Types of Phishing Attacks
Phishing attacks come in various forms, each with its specific approach to lure and deceive targets. Here are some of the most prevalent methods:
1. Email Phishing
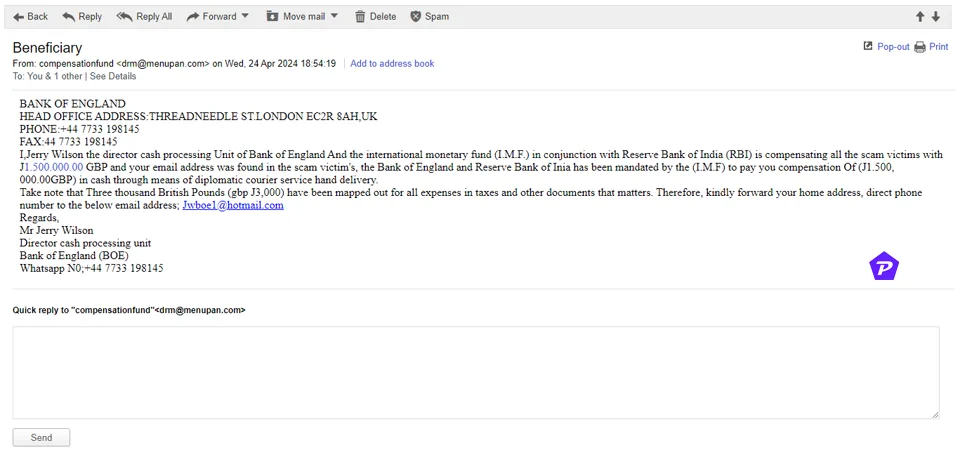 Email phishing is one of the oldest forms of phishing, targeting individuals through seemingly legitimate emails. Cybercriminals often create emails that appear to come from trusted sources like banks, government agencies, or popular retailers.
Email phishing is one of the oldest forms of phishing, targeting individuals through seemingly legitimate emails. Cybercriminals often create emails that appear to come from trusted sources like banks, government agencies, or popular retailers.
Characteristics:
- Often asks users to click a link, download an attachment, or provide login information.
- Increasingly well-crafted due to AI, making them harder to detect.
- Can include official logos, realistic subject lines, and even personalized greetings.
How to Protect Yourself:
- Verify the sender’s email address.
- Avoid clicking on links or attachments from unknown sources.
- Contact the organization directly if you suspect fraud.
2. Smishing
Smishing, or SMS phishing, involves using text messages to carry out phishing attacks. With people often assuming texts are personal or urgent, smishing scams have high success rates.
Common Smishing Tactics:
- Notifications about package deliveries, often with tracking links.
- Messages from “banks” alerting users of unusual account activity.
- Messages from strangers aiming to start a conversation.
Notable Example: Pig Butchering:
- A popular smishing scam where attackers build a relationship over time, then persuade the victim to invest in a fake cryptocurrency exchange.
Protection Tips:
- Avoid clicking on links in unsolicited texts.
- Confirm any alerts by visiting official websites or apps.
- Use anti-spam filters available on most mobile devices.
3. Angler Phishing
Angler phishing occurs on social media platforms where attackers pose as legitimate customer service agents to exploit users who seek help or post about issues with a brand or service.
Angler Phishing in Action:
- A fake customer service account reaches out to you with a “solution” for your problem.
- The scammer may provide a fake link to a login page to collect your credentials.
How to Recognize Angler Phishing:
- Look for subtle differences in usernames (extra letters, symbols).
- Verify social media accounts before sharing sensitive information.
- Only respond to verified customer service profiles with a blue checkmark.
4. Vishing
Vishing, or voice phishing, is where attackers call individuals under the pretense of being from a reputable organization like a bank, government agency, or technical support.
How Vishing Works:
- Attackers claim urgent scenarios, like fraud alerts or technical issues, to create a sense of urgency.
- They might ask for your Social Security number, account details, or other sensitive information.
How to Safeguard Against Vishing:
- Hang up and call the official customer support number of the organization.
- Be wary of unsolicited calls requesting personal information.
- Utilize scam-blocking features available on most smartphones.
5. Spear Phishing
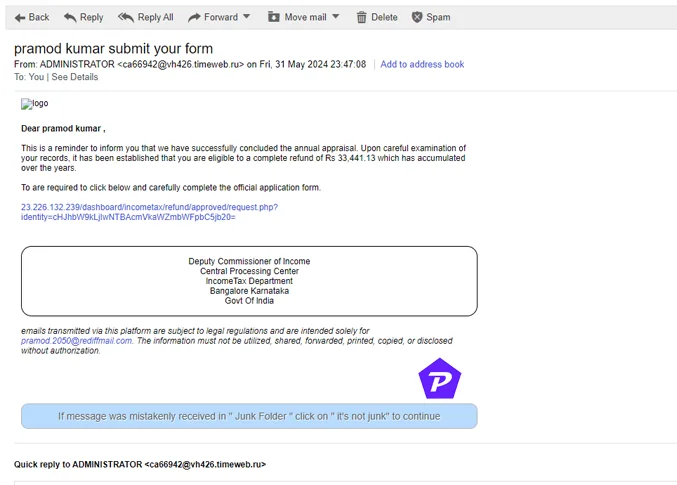
Unlike traditional phishing, spear phishing is highly personalized and targets specific individuals or groups. Attackers gather detailed information on their targets, like their job title, colleagues, or recent activities, to create a convincing message.
Specialized Attack Variants:
- Whaling: A subtype of spear phishing targeting high-profile individuals, often C-level executives or other high-ranking officials.
Example Scenario:
- An email that appears to come from a known colleague, asking for sensitive details or a quick wire transfer.
Protection Measures:
- Verify requests from colleagues or clients using alternative communication methods.
- Be cautious of unusual requests, even if they appear to come from a known contact.
6. Watering Hole Attacks
In a watering hole attack, cybercriminals compromise a trusted website frequented by the target audience, embedding malware or malicious links into the site’s code.
Why It’s Effective:
- Victims visit the website naturally, unaware that it has been compromised.
- Attackers may target industry-specific sites to reach a particular demographic.
Prevention Tips:
- Regularly update your browser and security software.
- Limit interactions on sites showing unusual behavior, like unexpected pop-ups or redirects.
7. Website Spoofing
Website spoofing occurs when attackers create a website that closely resembles a legitimate site to trick users into entering their sensitive information. Typosquatting, where attackers use domain names similar to popular sites, is a common tactic.
How Website Spoofing Works:
- Users mistype a URL (e.g., “Amazonn.com” instead of “Amazon.com”) and are redirected to a fake site.
- Spoofed sites look authentic but are designed to capture login credentials, payment details, or personal information.
Protective Measures:
- Double-check URLs before entering personal information.
- Enable two-factor authentication on sensitive accounts.
- Use a password manager to ensure you’re on legitimate sites.
Common Warning Signs of Phishing Attacks
Recognizing phishing attempts can help protect against falling victim. Here are a few red flags to watch for:
- Suspicious Email Addresses: Look for misspellings or extra characters in domain names.
- Urgent Language: Phishing messages often urge immediate action.
- Generic Greetings: Phrases like “Dear Customer” instead of using your name.
- Unexpected Attachments or Links: Avoid clicking on attachments from unknown senders.
- Grammar and Spelling Errors: While some attacks are sophisticated, errors can still be a sign of fraud.
How to Protect Yourself from Phishing Attacks
- Enable Multi-Factor Authentication (MFA):
- Adding an extra layer of security makes it harder for attackers to access your accounts.
- Educate Yourself and Others:
- Stay informed on phishing tactics and educate family and colleagues on recognizing suspicious messages.
- Use Anti-Phishing Tools:
- Many email providers offer built-in phishing detection. Additionally, anti-virus software often includes anti-phishing protection.
- Verify Requests for Information:
- If you receive a request for sensitive information, verify it through an official communication channel.
- Regularly Update Your Software:
- Security patches protect against known vulnerabilities that attackers exploit.
Conclusion
Phishing has evolved from simple email scams into a multifaceted online threat, targeting victims across multiple platforms. Understanding the nuances of each phishing type—from smishing to watering hole attacks—empowers individuals to recognize and avoid these schemes. By remaining vigilant, you can reduce the risk of falling prey to these increasingly sophisticated attacks.
When you purchase through links on our site, we may earn an affiliate commission. Read our Affiliate Policy.




